Email scams have now netted more than $43 billion, says FBI


Victoria Rees
Share this content
In a new public service announcement, the Federal Bureau of Investigation (FBI) said that the amount of money lost to business email compromise (BEC) scams continues to soar with a 65% increase in reported global exposed losses between July 2019 and December 2021. That is more than double the losses for the previous three years and the true figure is likely to be significantly higher.
Scammers are targeting small local businesses and larger corporations as well as personal transactions. “The increase can be partly attributed to the restrictions placed on normal business practices during the COVID-19 pandemic, which caused more workplaces and individuals to conduct routine business virtually,” says the report.
“This Public Service Announcement is an update and companion piece to Business Email Compromise PSA I-091019-PSA posted on www.ic3.gov. This PSA includes new Internet Crime Complaint Center complaint information and updated statistics from October 2013 to December 2021.”
It names banks located in Thailand and Hong Kong as the primary international destinations of fraudulent funds. China, was the top destination until this new study, and is now in third top two destinations in previous years, ranked third in 2021, followed by Mexico and Singapore.
From June 2016 until July 2019, IC3 received victim complaints regarding more than 241,000 domestic and international incidents, with a total exposed dollar loss of over $43 billion, according to the FBI.
BEC attacks, also known as CEO/CFO fraud, is financial in nature and targets organisations of all sizes The basic game plan is to pretend to be someone at executive level, and then convince an employee to help them wire funds outside of the company.
As the FBI points out, the goal is not always a direct fund transfer: Two iterations of the BEC scam where cryptocurrency was utilized included a direct transfer to a cryptocurrency exchange (CE) or a “second hop” transfer to a CE. The victim is unaware that the funds are being sent to be converted to cryptocurrency in both situations.
Scammers are employing various tactics — including social engineering, phishing, and hacking — to compromise business email accounts which will get used to redirect payments to attacker-controlled bank accounts.
(continues below picture)
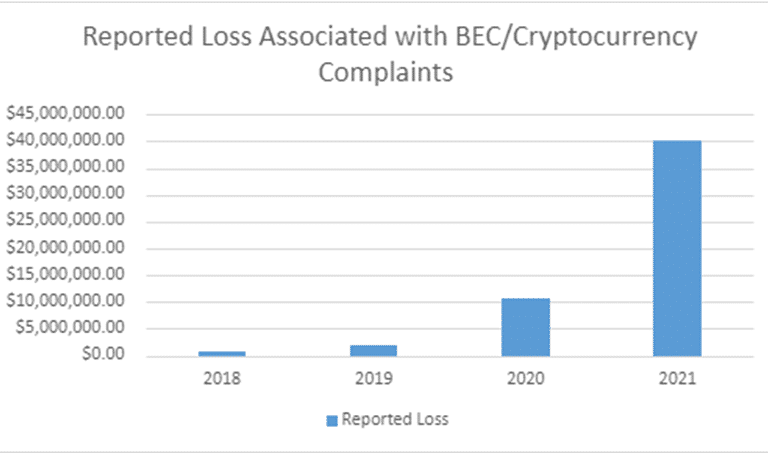
Success rates are high, given that they generally impersonate someone who has the target’s trust, such as business partners or company executives.
The FBI also provided guidance on how to defend against BEC scam attempts:
- Use secondary channels or two-factor authentication to verify requests for changes in account information.
- Ensure the URL in emails is associated with the business/individual it claims to be from.
- Be alert to hyperlinks that may contain misspellings of the actual domain name.
- Refrain from supplying login credentials or PII of any sort via email. Be aware that many emails requesting your personal information may appear to be legitimate.
- Verify the email address used to send emails, especially when using a mobile or handheld device, by ensuring the sender’s address appears to match who it is coming from.
- Ensure the settings in employees’ computers are enabled to allow full email extensions to be viewed.
- Monitor your personal financial accounts on a regular basis for irregularities, such as missing deposits.
The federal law enforcement agency advises those who fall victim to BEC fraud to immediately reach out to their bank to request a recall of funds.
They’re also urged to file a complaint with the FBI at BEC.ic3.gov, regardless of the lost amount, and as soon as possible.
READ THE FULL FBI REPORT AND ADVICE HERE
Return to the NEWS index for Security Journal Americas


